Unifying the Department of War
A Game and Network Theory Model for Restoring Constitutional Fidelity
Executive Summary
A common understanding of institutional control within the federal government relies on the assumption that employees can be counted on to well and faithfully execute the intent of those occupying positions of Constitutional authority. This understanding does not conform to reality. This essay argues that a model incorporating game and network theories facilitates essential understanding of how Constitutional authority can be practically converted into institutional power and control within the Department of War (DOW). Further, it argues that developing shared understanding based upon this model can help senior leaders in their ongoing efforts to align the DOW with its Constitutional role as understood by good faith legal and political analysts, the Commander-in-Chief, and all patriotic Americans. By framing the erosion of apolitical norms as a one-sided defection in a repeated game, exacerbated by network imbalances favoring progressive ideologies, and informed by the relationship between incompetence and malice described by Grey's Law and cybernetic principles, this framework empowers the Secretary of War to implement key reforms. These include conducting targeted audits based on the results of comprehensive social network analysis (SNA), enforcing uniform accountability to Constitutional imperatives, and making aggressive use of hierarchical control to offset power emanating from misaligned informal networks to enhance organizational performance towards achieving unified purpose under lawful authority.
Game Theory: A Context-Specific Primer
Game theory is the mathematical study of strategic interactions among rational decision-makers, where the outcome for each participant depends on the choices of all involved. Developed by pioneers like John von Neumann and Oskar Morgenstern in the 1940s, it models scenarios as "games" with players, strategies, and payoffs, analyzing how individuals or groups anticipate and respond to others' actions to maximize their own benefits. Core concepts include the Nash equilibrium, where no player benefits from unilaterally changing strategy, and the Prisoner's Dilemma, which illustrates how rational self-interest can lead to suboptimal collective outcomes, such as mutual defection instead of cooperation.
Beyond economics, game theory applies broadly to fields like biology, politics, and international relations, providing tools to predict behaviors in competitive or cooperative settings. In military strategy, game theory has long informed deterrence, arms races, and conflict escalation, as seen in Cold War models of mutually assured destruction where nations weigh the costs of aggression against retaliation. For instance, repeated games help explain alliance stability, where ongoing cooperation yields mutual security but defection—such as betrayal or unilateral disarmament—triggers cascading distrust.
Applied to norms of political neutrality in institutions like the U.S. military, these frameworks reveal how apolitical traditions function as a cooperative equilibrium: service members and leaders from diverse ideologies mutually refrain from partisanship to preserve institutional trust and operational cohesion. However, as highlighted in analyses of recent U.S. military dynamics, this equilibrium breaks when one side defects by injecting ideology into promotions, training, or enforcement, prompting rational anticipation of future betrayals and eroding the "gentleman's agreement" of neutrality. This defection against apolitical norms was subtly achieved and concealed by reframing progressive and extreme egalitarian assumptions—such as the utility of diversity, equity, and inclusion (DEI) mandates, open transgender military service, and draconian COVID-era policies—as inherently "apolitical" universal goods, rather than the counter-productive progressive cultural embedding mechanisms they truly represent.1
By embedding progressive political assumptions into ostensibly neutral policies justified in the name of readiness, accountability, and merit-based selection, proponents masked their ideological bent, portraying dissent as extremism while advancing factional agendas under the guise of legitimate duty. This sleight-of-hand, evident in Biden-era directives and congressional testimonies on progressive ideologies' risks, allowed selective enforcement—punishing conservative-leaning expressions while tolerating or promoting left-leaning ones—thus paradoxically normalizing bias in the name of neutrality.2
This environment of enforced one-sided defection against apolitical norms represents the status quo inherited by current senior leadership, and it will not change without deliberate effort directed towards deterring such defection against Constitutionally required norms. Centering norms on adherence to Constitutional requirements properly frames promotion of DEI, transgender inclusion, and COVID-era policy as the defections against essential political neutrality that they are. Only through the enforcement of such norms alongside the application of robust accountability mechanisms for defection can the environment within DOW be shifted towards a Constitutionally aligned cooperative equilibrium.
Network Theory: A Context-Specific Primer
Network theory, a branch of mathematics and social sciences, examines the structure and dynamics of interconnected systems by modeling them as graphs consisting of nodes (entities such as individuals or organizations) and edges (relationships or interactions between them). Originating from graph theory and expanded in the mid-20th century by scholars like Stanley Milgram through concepts like "six degrees of separation," it analyzes how patterns of connectivity impact information flow, influence, and resilience in complex systems. In social network analysis (SNA), a key subset, nodes represent people or groups, while edges denote ties like friendships, collaborations, or hierarchies, revealing phenomena such as clustering (dense subgroups) or centrality (nodes with high connectivity that act as hubs).
This framework highlights emergent properties, like how small-world networks facilitate rapid information spread, and scale-free networks exhibit power-law distributions where a few highly connected nodes dominate.3 The U.S. military can be conceptualized as a vast social network where nodes comprise individual service members, federal civilian employees, contractors, and even allied entities, linked by edges representing formal hierarchies (e.g., command chains), informal relationships (e.g., mentorships or social bonds), and operational collaborations (e.g., joint exercises or deployments). Social network analysis has been applied to military organizations to map command-and-control structures, identify key influencers in decision-making, and assess cohesion in units, as seen in studies of headquarters dynamics4 and counterterrorism operations.5 In this network, central nodes—such as senior officers or policy influencers—wield disproportionate power through their high degree of connections, while peripheral nodes (e.g., junior enlisted personnel) contribute to overall resilience but are more vulnerable to disruptions.
This structure fosters trust and efficiency when edges are merit-based and Constitutionally aligned, but imbalances can propagate biases, amplifying the influence of clusters aligned with rival ideologies. Over the past 20-30 years, a one-sided defection from apolitical norms—manifesting as the integration of progressive ideology through policy—has eroded neutrality, enabling the consolidation of power in progressive-leaning nodes through the mechanics of associative network formation and preferential attachment. Associative networks, driven by homophily (the tendency for similar nodes to connect), allowed progressive advocates to form dense clusters by framing partisan values as universal legal, moral, and ethical imperatives, attracting attachments from aspiring careerists seeking advancement and fellow ideologues alike. Preferential attachment, where new nodes preferentially link to already well-connected hubs, exacerbated this: early defectors in high-centrality positions (e.g., DoD leadership roles) gained visibility and resources, drawing further allegiance and sidelining conservative or neutral nodes cast as "extremist" or “unprofessional” for dissenting. Surveys indicate this has resulted in widespread perceptions of politicization, with 68% of service members witnessing moderate to significant bias, leading to fractured trust and a scale-free tilt where progressive hubs dominate influence, potentially undermining operational cohesion.6
This network imbalance makes the military vulnerable to operational fragility, as historical precedents show politicized militaries fracture under stress. It also subverts control by legitimate Constitutional authority, by diverting the flow of power away from the formal, legible chain of command into comparatively durable and illegible informal nodes. A politically fragile military undermines national security. That is to say from its inception, the permanent bureaucracy has been structurally enabled to establish robust networks initially associated around their de facto managerial class interest7, then further strengthened by preferential attachment. These networks are accordingly highly resistant to influence and direction from political appointees when their interests are misaligned, as might be expected under populist leadership. While the formal hierarchy does comprise important edges in the overall network, they will be outnumbered by misaligned informal edges by orders of magnitude without aggressive intervention.
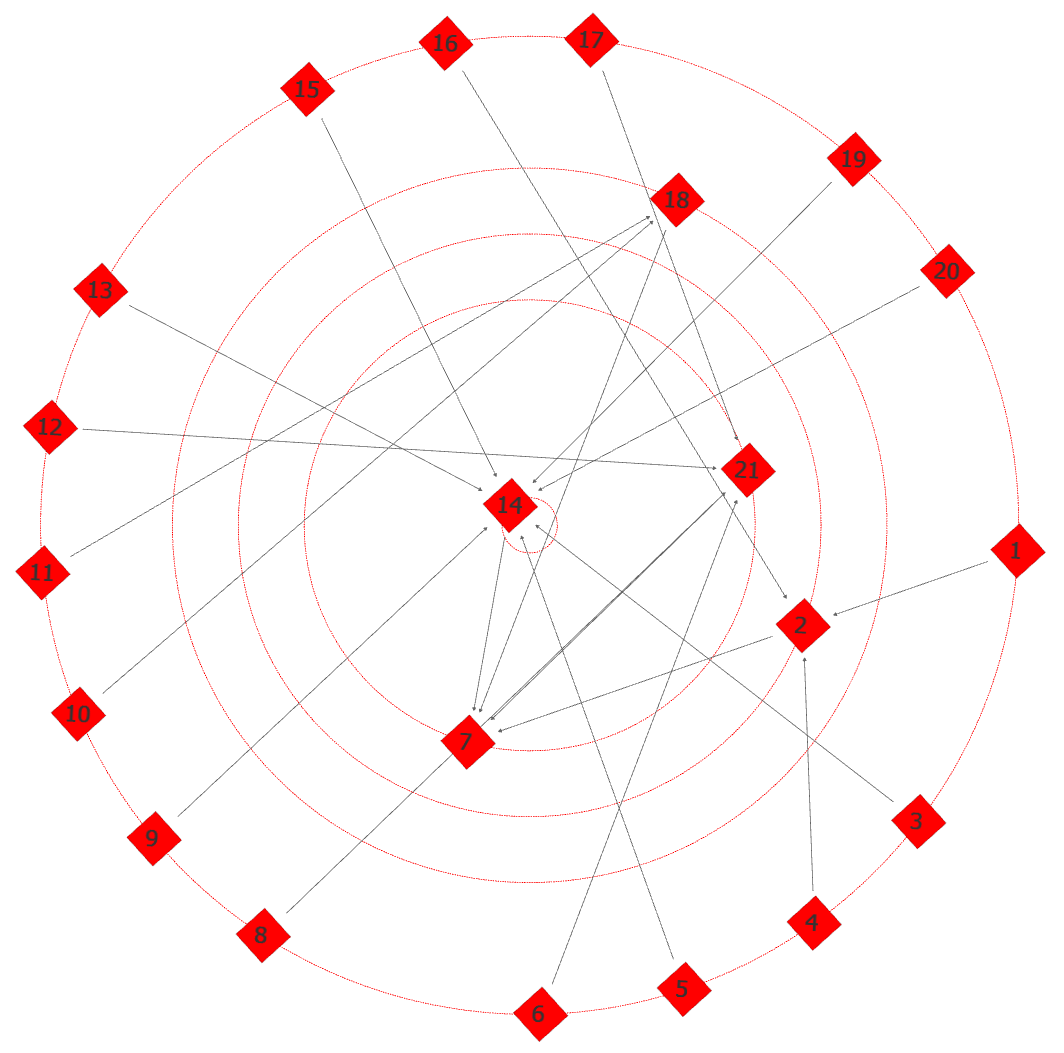
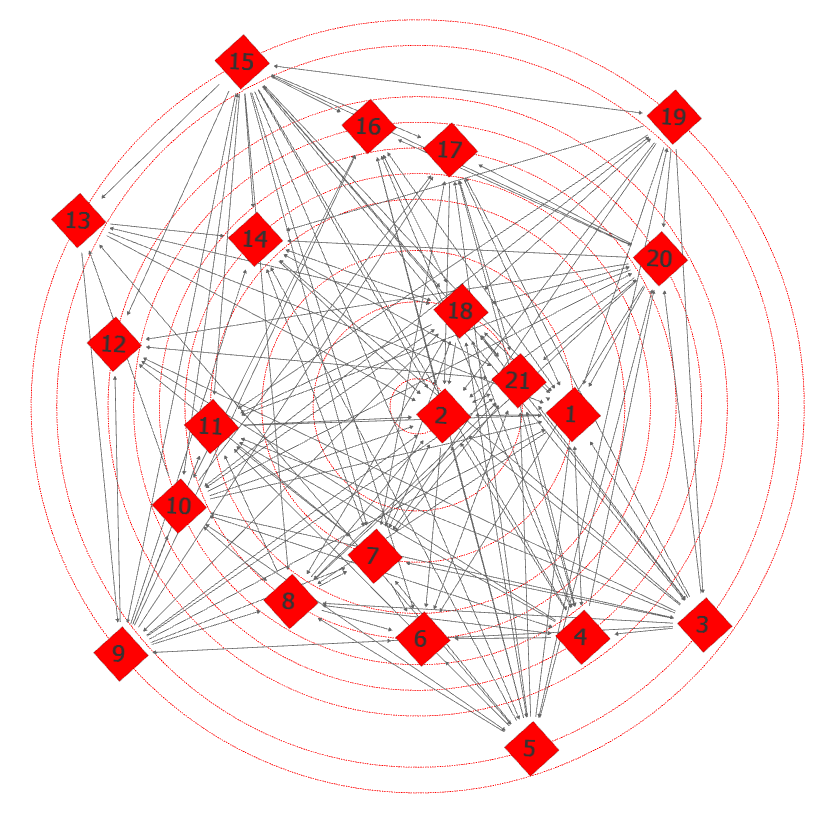
To better visualize this concept, we can consider example network graphs arranged radially by Degree Prestige (nodes with the most inbound edges most central) from sample data loosely applicable to a military headquarters or department.8
For illustration purposes, consider the top graph to depict formal reporting relationships in a military hierarchy, and the bottom graph to depict informal relationships. Note how the central most node shifts dramatically between these examples, demonstrating the extent to which organizational influence can rest predominantly outside the hands of the chief executive. In such a circumstance, the disproportionate influence of the formal hierarchy would need to be fully leveraged to wrest control from unaligned nodes wielding significant informal power where time constraints are a factor given the rate limited nature of building such relationships organically. I should also note that if one were to conduct a social network analysis of the Pentagon, the differential between formal and informal edges would almost certainly be much larger, reflecting the nature of scale-free networks more adequately than this limited example.
Grey’s Law and the Cybernetic Approach to Intent
Grey's Law, a satirical extension of Arthur C. Clarke's Third Law and Hanlon's Razor, posits that "any sufficiently advanced incompetence is indistinguishable from malice." Coined in online discourse and tech communities, Grey’s Law warns against the assumption that deliberate hostility can be disentangled from profound systemic bungling, cognitive biases, or unintended cascading errors within complex systems. In network theory terms, this law underscores how poorly managed interconnections—such as misaligned incentives or unchecked homophily—can amplify minor flaws into apparent conspiracies, eroding trust with or without ill intent. In other words, Grey's Law recognizes that differentiating between malice and incompetence in complex systems is often impossible, making it a lens for impartially dissecting imbalances in social graphs where power accrues inappropriately.
In the U.S. military's social network, the established imbalance—where progressive values have consolidated influence in central nodes like policy hubs and promotion pathways—exemplifies Grey's Law in action. Over decades, what began as subtle unconscious bias towards pursuing group interest alongside fulfilling duty ended in widespread defection from Constitutional norms. While there are certainly individuals who have become acutely aware of the limitations the Constitution imposes upon their ideological agenda making subsequent defection malicious and deliberate, they are difficult to differentiate from those who ultimately defected out of ignorance, incompetence, and narrow career-oriented self-interest.9
To avoid getting mired in the ambiguity between malice and incompetence explained by Grey’s Law, we can use a key analytical tool from the field of cybernetics to cut through the noise. Coined by cyberneticist Stafford Beer, the “purpose of a system is what it does” or POSIWID for short, is a descriptive principle used to clarify the futility of assessing what complex systems ought to do by focusing instead on what they actually do. This helps clarify that the focus of reform should be on what the system is actually doing, not what it should be doing. We all know what the DOW should be doing, as it is outlined clearly by the Constitution. This helps us focus on what it is actually doing, and that is in certain key areas, subverting lawful Constitutional authority. To put the two concepts together, we don’t have to differentiate between malice or incompetence to evaluate the system descriptively based on definitive observations. When these observation demonstrate significant delta between ought and is, skillful application of cybernetic control becomes necessary to close the gap.
Discussion
We serve in a military that allowed Constitutionally appropriate Equal Opportunity programs to warp into divisive DEI policy, successful racial and gender integration to transform into counterproductive accommodation of “dudes in dresses”, and Constitutional authority to direct operationally justifiable medical interventions to metastasize into unlawfully implemented mandates of dubious benefit. While focus was directed towards facilitating these perverse trends, years of operational failure to achieve meaningful results in the Global War on Terror culminated in the disastrous withdrawal from Afghanistan. Whether leadership deliberately ignored the partisan political implications of these policies or simply failed to recognize them is irrelevant with respect to the outcome. The result was a normalization of defection from apolitical norms resulting in a scale-free tilt10 across the social network towards progressive ideological alignment at the expense of organizational effectiveness.
Progressive clusters gained preferential attachments from careerist nodes mistaking ideological conformity for merit, while dissenting nodes were isolated if not eliminated entirely for maintaining loyalty to their oaths.11 The result suggests the influence of malice—selective purges and fractured cohesion—but Grey's Law reveals how incompetence, ignorance, and apathy worked in parallel with conscious, ideologically driven sabotage. Applying this recognition to network warfare reframes the optimal strategy from combative disruption (which risks entrenching defensive clusters) to corrective realignment, treating the imbalance as correctable incompetence rather than an irredeemable foe where direct evidence of malice is absent. In other words, it allows us to see that there are similar consequences for defection whether or not we can definitively determine what motivated it. Simultaneously, it highlights that this limitation must not be an obstacle to the establishment of accountability mechanisms to disincentivize defection and heal the damage done to the network by unchecked and Constitutionally incompatible political ideology.
In addition to reactive establishment of accountability mechanisms, proactive measures such as bolstering edges connecting to “Constitutionally faithful” nodes can leverage small-world properties for rapid influence diffusion without alienating incumbents. Tactics include transparent audits centering on competence evaluation and constitutional fidelity aimed at public exposure of defection to enable subsequent pruning of edges and nodes as informed by audit results. This approach culminates in a Nash-like equilibrium where power centers realign with lawful nodes: by amplifying nodes that model neutrality and suppressing nodes that model defection, the network self-heals, diluting progressive dominance without nominally ideological purges that could trigger backlash cascades.
Recommendations
To apply this model effectively, the DOW should prioritize actions that convert theoretical insights into practical reforms, enhancing leadership and fulfilling the DOW's Constitutional purpose.
First, commission a comprehensive social network analysis (SNA) of the DOW using internal data and external expertise to map ideological clusters, centrality biases, and preferential attachments. This is an essential step towards understanding the current purpose in the sense of POSIWID to apprehend the current gap between ought and is. Focus targeted audits on Constitutionally misaligned hubs oriented towards determining discrete behaviors consistent with defection to identify nodes requiring retraining and elimination to close gaps identified by the analysis.
Second, enforce uniform standards through mandatory, transparent reviews of promotions, training programs, extremism classifications, and performance. For example, consider how performance is measured in critical areas like warfighting and expeditious execution of administrative actions, make any changes necessary to ensure deviation from standards is objectively identifiable, and enforce with meaningful consequences. Clarify that DEI, COVID policy, and transgender policy warrant increased scrutiny in regards to the enforcement of these standards not because of their partisan valence, but because they represent dramatic defections from neutrality that must be addressed effectively to disincentivize continued defection and restore trust.12
Third, recognize the gross asymmetry of power-laws and what this entails for the social network comprising the DOW to justify aggressive use of hierarchical control to offset power emanating from misaligned informal networks. For example, if misaligned hub nodes are identified, use available authority to remove the node via termination accepting the disruption to the network this entails as necessary and beneficial “creative destruction”. Further, foster the development of aligned informal networks by incentivizing mentorships and leadership programs that develop a shared understanding of Constitutional fidelity and the sanctity of the oath. For example, deploy Constitution oriented training including realistic vignettes where conflicts exist between progressive ideology and Constitutional fidelity to clarify obligatory conduct to obviate ignorance as an excuse for noncompliance and generate cognitive dissonance in misaligned nodes. Reward behaviors demonstrating this fidelity at echelon to attract new attachments to neutral hubs and leverage small-world diffusion for cultural shift.
Fourth, throughout implementation of these reforms, integrate Grey's Law and POSIWID by focusing on objective outcomes inconsistent with the DOWs mission in lieu of attempting to differentiate between incompetence and malice where it is unclear. Treat identified deviations from standards as incompetence first—offering retraining for minor infractions while aggressively removing nodes exhibiting malice, such as those celebrating political violence. Monitor progress via anonymous surveys and key performance indicators oriented around objective warfighting capability, adjusting iteratively to achieve a Nash equilibrium of mutual cooperation in pursuit of Constitutional imperatives.
Historical successes, such as post-Vietnam reforms, underscore that these competence-focused interventions will restore resilience, empower patriotic service members, and realign the DOW with its core mission: safeguarding the nation under lawful civilian authority. By embracing this framework, the DOW can transform inherited imbalances into a legacy of restored integrity and unparalleled warfighting proficiency.
https://www.nraila.org/articles/20250421/declassified-document-biden-harris-administration-targeted-gun-owners-and-second-amendment-rights-under-domestic-terrorism-pretext
https://oversight.house.gov/hearing/the-risks-of-progressive-ideologies-in-the-u-s-military/
Power-law distributions are rare in nature and contrast sharply with normal distributions that conform to a “bell curve”. In terms of networks, it explains why the most highly connected nodes in a given network might have hundreds or thousands more connections than those in the middle of the distribution. To compare to an attribute with a normal distribution, human height, we can see that the tallest person in the world isn’t even twice as tall as those in the middle of the distribution. While counterintuitive, the distribution of power within social networks has profound implications.
https://www.researchgate.net/publication/2317708_Social_Network_Analysis_in_Military_Headquarters_using_CAVALIER
https://scholar.afit.edu/cgi/viewcontent.cgi?article=1107&context=etd
https://www.heritage.org/defense/report/poll-nearly-seven-10-active-service-members-have-witnessed-politicization-us
In the early days of the managerial revolution, the managerial class did not have a single unifying ideology. Rather, as power accrued within the managerial class in no small part due to network effects, justification for their disproportionate power and influence became essential to the continued advancement of their class interest. Progressive humanitarian ideals fit this role perfectly, becoming the raison d’etre of the managerial class.
Krackhardt's High-tech Managers Networks (1976) https://www.network.data.ics.uci.edu
Unless they share these sentiments on social media as we have seen recently.
A scale-free network is simply one that follows power-law distribution. The rise of social media contributed to the development of this tilt in social networks, and towards progressive ideologies in particular from around 2017 thanks to targeted censorship directed against against populist voices through what Mike Benz calls the “censorship industrial complex”. Within the military, this phenomenon can be readily understood by considering the nature of the discourse on “miltwitter” during this timeframe and extending through Elon Musk’s purchase of the platform.
Read: COVID-era separations
Focus on objective deviation from norm characterizing defection, not particular political slant. Extremism investigations in 2021 violated this principle in dramatic fashion.

The purpose of a system is what it does.
I would say that in tort law, the main standard is negligence - could a reasonable person have prevented the something bad from happening. Intent more or less is irrelevant, if you are negligent, you are responsible for the damage.